- 10+ способов создания отчётов в Microsoft Dynamics CRM
- Революционная «пятёрка»
- Solution Management – управление компонентами в CRM5
- Microsoft Dynamics CRM 2011 - официальный показ
- 13 добродетелей Бенджамина Франклина
- Пароль «Рыба-меч» – защищаем секретные значения в CRM
- Использование механизма Smart Tag для интеграции приложений Microsoft Office с CRM
Пароль «Рыба-меч» – защищаем секретные значения в CRM
В продолжение поста "Поле-пароль" описывающего скрипты, скрывающие хранимый в записи CRM пароль пользователя.
Текущая версия Microsoft Dynamics CRM не поддерживает т.н. field level security - разграничение прав доступа на уровне полей конкретной сущности. Ролями безопасности настраивается доступ ко всей сущности. Часто возникают ситуации когда требуется защитить/скрыть часть полей от определённых групп пользователей CRM. Для таких случаев предлагается заводить отдельную сущность (она будет хранить секретные значения), привязывать её к основной сущности, и на уровне ролей безопасности раздавать права обычным и привилегированным пользователям.
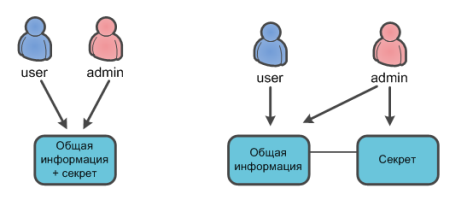
Данная реализация не всегда удобна.
Рассмотрим такой сценарий: требуется хранить девичью фамилию матери контакта в CRM, причём операторы CRM не должны его видеть, но иметь возможность сопоставить значение с хранимым в CRM (например, полученное от клиента во время телефонного звонка - стандартная ситуация при обслуживании в банке по телефону).
Понятно, что хранить фамилию открытым текстом не следует. Но в поле с ответом (для значения девичьей фамилии, хотя это может быть любое секретное значение, в том числе и пароль) можно поместить хэш (контрольную сумму), рассчитанную для конкретной фамилии.
Хэш-суммой или дайджестом сообщения называется значение хэш-функции на тех или иных данных. Хэширование — преобразование входного массива данных произвольной длины в выходную битовую строку фиксированной длины.
Таким образом, вместо открытого значения "Иванова" в CRM будет сохранено "jCVf/9aS9M+zSUeg/gBBZ/nrvIg=". Тогда для проверки названного клиентом значения, необходимо рассчитать для него по тому же алгоритму хэш-сумму и сравнивать не сами фамилии, а их хэш-значения.
Рассмотрим пример реализации вышеописанного.
Для вычисления хэша значения воспользуемся типом System.Security.Cryptography.HMACSHA1 из библиотеки классов .NET Framework. Данный класс вычисляет хэш-код проверки подлинности сообщения (HMAC) с помощью хэш-функции SHA1.
HMACSHA1 hash = new HMACSHA1(); // используем алгоритм с ключём; значение ключа можно хранить в конфигурационном файле hash.Key = GetSHA1Key(); // получаем значение для которого будет вычислен хэш string secretText = "Секретное_значение_девичьей_фамилии_матери"; // вычисляем хэш, для удобства конвертируем его в строку Base64 string hashValue = Convert.ToBase64String(hash.ComputeHash(Encoding.Unicode.GetBytes(secretText)));
Далее хэш-код спокойно храним в CRM. Реконструировать секрет по дайджесту нельзя (т.к. это результат односторонней функции). Значение этого хэша никому не интересно, его можно, разве что, только «испортить» или удалить, но сам секрет так и останется неизвестным.
В час Икс клиент называет секретное значение, которое надо сравнить с имеющимся в CRM. Для чего рассчитываем хэш для названного клиентом секрета по тому же самому алгоритму. И если хэш-суммы совпадают, значит и девичья фамилия матери названа клиентом верно (предполагается, что оператор использует утилиту для расчёта хэша, например, реализованную на crypto-js).
Теперь, представьте, что вместо оператора колл-центра, и девичьей фамилией матери у нас доступ к личному кабинету клиента по паролю... Ничего не меняется, за исключением того, что вычисление и проверка хэшей производится автоматически, и секретное значение остаётся известным только самому клиенту.
HMACSHA1 — это хэш-алгоритм с ключом, созданный на основе хэш-функции SHA1 и используемый для вычисления хэш-кода проверки подлинности сообщения (HMAC).
Процесс вычисления кода HMAC заключается в смешивании секретного ключа с данными сообщения, вычислении хэш-функции результата, повторном смешивании хэш-значения с секретным ключом и повторном применении хэш-функции. Длина выходного хэша составляет 160 бит.
Код HMAC может использоваться для выявления факта подделки сообщения, передаваемого по незащищенному каналу, при условии, что секретный ключ известен отправителю и получателю. Отправитель вычисляет хэш-значение исходных данных, а затем передает исходные данные и хэш-значение в одном сообщении. Получатель повторно вычисляет значение хэша полученных данных и проверяет, совпадает ли оно с полученным кодом HMAC.
Любое изменение данных или значения хэша вызовет несовпадение, поскольку для изменения сообщения и повторного создания правильного кода HMAC необходимо знать секретный ключ. Таким образом, если исходное значение хэша совпадает с вычисленным, считается, что подлинность сообщения установлена.
SHA-1 (Secure Hash Algorithm; другое название — Secure Hash Standard, SHS) является криптографическим хэш-алгоритмом, опубликованным правительством США. Он используется для формирования 160-разрядных хэш-значений из строк произвольной длины.
На вход HMACSHA1 подаются ключи любой длины, на выходе формируется хэш-значение длиной 160 бит.

Комментарии
Андрей a33ik Бутенко (не проверено)
18.03.2010 12:48
Permalink
Field Level Security можно
Field Level Security можно разработать. Всего то надо 3 плагина - на Execute, RetrieveMultiple и Retrieve. Также необходимо пересмотреть всю существующую отчётность и переработать её в соответствии с настройками Field Level Security. http://a33ik.blogspot.com/2009/06/field-security-level-with-own-hands.html - было сделано по сути за день работы. Не идеал конечно.
Добавить комментарий